During an engagement, having an email list for your target can be useful for a variety of reasons. When it comes to social engineering and password spraying, more email addresses translate to higher chances of success. While some clients will provide an employee directory, for others it may be necessary to use other resources to obtain a working list.
Old School
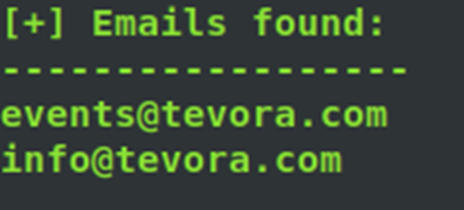
Traditional email reconnaissance tools such as theHarvester work by scraping multiple search engines for any addresses that match a user-provided domain. However, depending on the online presence of the organization, these types of tools may only find a few or none at all. Running theHarvester against tevora.com with all options enabled didn’t turn up any useful results.
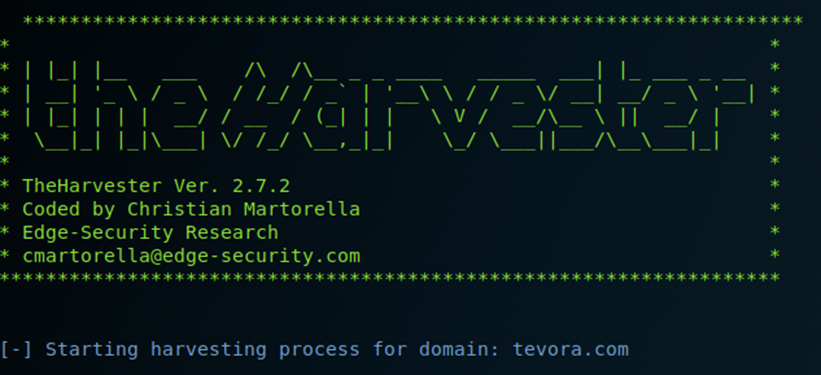
Nothing useful here
New School
While a company as a whole may be good about keeping the net clear of usable data, their individual employees usually aren’t. Social media has increasingly become useful for OSINT and it would be foolish to ignore it. An email harvesting tool using a different approach, Prowl, written by Matt Pickford, takes advantage of employees sharing about their workplaces online to compile usable email lists.
Prowl works by scraping Bing and Yahoo for the LinkedIn profiles of people who currently work at the target organization, then converts their names into email addresses following a preconfigured format. Since people are much more likely to disclose their employer than their work email this often pulls significantly better results.
Two caveats, however: Prowl requires knowledge of the address format in use by the organization and the resulting emails are not guaranteed to be valid. The first issue can be solved by enumerating enough emails the traditional way (such as with theHarverster) to determine the structure, or, more easily, by looking at the contact info for the client. For the second issue, some addresses can be manually fixed if the LinkedIn user entered their name in a nonstandard way, otherwise there’s no other way to know if the organization deviated from the standard convention when creating the individual’s account. Fortunately, the quantity of valid addresses will usually outnumber the false positives.
The Test
Configuring Prowl is straightforward, with the company specified with the -c flag and the email string with the -e flag. Names or initials are inserted as variables such as <fn> for first name and <li> for last initial. Search depth measured in search engine pages can be set with -d.
./prowl.py -c Tevora -e "<fn>.<ln>@tevora.com" -d 10
No point in censoring when you can run it for yourself
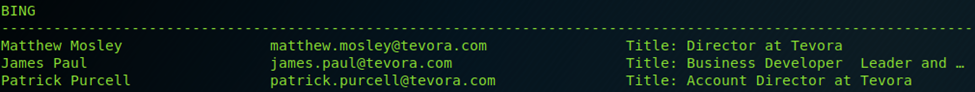
Of the results from searching against Tevora, more than half of the emails generated were legitimate. Considering the lack of hits generated by theHarvester, this is definitely an improvement. Most of the false positives were from people no longer with the company, not incorrect generation, so this is hardly the tool’s fault. Overall, Prowl provided valid emails for nearly half of the organization, which is both impressive for the tool and an interesting commentary on the impact of social media.