Background
Password cracking is a crucial part of a pentest. It can either lead you to the promised land, or stop you dead in your tracks. Password cracking is somewhat of an art, but there are some ways to make the process objectively better, so you can focus on more pwning. We'll discuss how you can take a budget build and turn it in to an effective tool for your pentesting arsenal.
To effectively crack passwords, you need to focus on 3 things:
- The Hardware
- The Wordlists
- The Rules
The Rig
Our day-to-day rig is a GPU powerhouse, but that's just not feasible for the hobbyist password cracker, and there are already plenty of great blog posts on building multi-thousand dollar cracking rigs. No use beating a dead horse, with another build blog.
However, for around $1200, you can build a decent rig around a single Nvidia GEFORCE GTX 1080 Ti.

The rest of the hardware doesn't need to be very special. This is what we recommend to build a rig on a budget:
- Nvidia GEFORCE GTX 1080 Ti
- This is going to be the most expensive piece of the rig at about $700.
- 250-500GB SSD
- SSD increases wordlist read speed, and they're getting cheaper by the day. Splurge if you can.
- Intel i5 or i7 CPU
- You're not gaining much performance by going to the i7, but if you got a little extra $$, go for it.
- 16GB RAM
- RAM is cheap, buy as much as you can afford and fit in your motherboard
- The special of the week motherboard and case combo from you favorite (local/online) hardware vendor
- You favorite linux flavor, and a copy of hashcat
Depending on how frugal you are, the rig will probably cost about $1200-$1500. Keep in mind that $700 of that cost is the GPU alone. This isn't too bad considering it's anywhere between $50 to $200 per day to run an AWS g2.8xlarge instance. Another nice benefit is that a single 1080 Ti, performs faster than the AWS g2.8xlarge instance. So, it's an all-around win if you're currently using a hosted cracking instance. Nothing against using AWS, it's just a better investment to build your own rig if you're planning on using it frequently.
We used the budget build hardware to run our test cases, so that we could show how effective this rig can be with the right wordlists and rules.
Finding the Perfect Wordlists
After putting together the hardware we needed to focus on finding the right wordlists to bring our cracking rate up to an acceptable percentage.
When we started building a test case for this blog, our original goal was to have a 33% crack rate. We use Responder during internal pentests, so cracking 1 out of every 3 NTLM hashes almost guarantees us a path to domain admin. This was our starting goal. To test this, we gathered 40 NTLMv2 hashes from recent pentests.
After some Googling and a little bit of trial and error, we found our wordlists. Here are the top 3 performers, from publicly available wordlists:
- Weakpass 2.0: https://weakpass.com/download
- Crackstation: https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
- Rockyou: included in Kali Linux - https://www.kali.org/downloads/
Yes, there are others that are bigger, but in our test case these were most effective when considering the time to number of cracks ratio.
Weakpass 2.0
Weakpass 2.0 is a combination of several dumps and available wordlists. This wordlist is huge, weighing in at 28GB. Weakpass 2.0 had the highest standalone crack rate with 14 of the 40 hashes cracked. That's 35% right from the start.
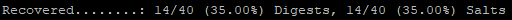
It takes about 4 minutes to run through the weakpass 2.0 wordlist with (1) 1080 Ti. FYI, there's a bit of time taken to cache the wordlist when hashcat first starts. However, this is VERY dependent on the supporting hardware.
There is also a "Weakpass 2.0 A", but this wordlist isn't worth it in most cases:
- "A" is 85GB compared to 2.0 at 28GB. Meaning it takes 3 times longer to run through.
- "A" has a 66.88% crack rate according to their site, as opposed to a 65.16% crack rate with 2.0. Only a 1.72% difference in crack rate, with a 66% difference in size.
- "A" contains 4-character passwords, while 2.0 only 5+ character passwords. 4-character passwords are not common for most organizations, and easy enough to brute force.
Stick with weakpass 2.0 for the best bang-for-your-buck. The time to crack rate ratio is better with 2.0.
Crackstation
Crackstation is another combination wordlist, weighing in at 15GB. This is a solid wordlist that had a standalone crack rate of 27.5% in our test case.
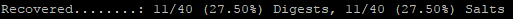
It only takes about 2 minutes to run through it, so it's worth giving it a shot. This wordlist is pretty stagnant, but it has been a solid performer for 2+ years now. We like it, it works, and you should check it out.
Rockyou
The RockYou wordlist is from the Rockyou.com breach. It was the largest dump of plaintext passwords at the time, and has been a quick go-to for several years now. It comes default with Kali Linux and, compared to the others above, it's tiny weighing in at only 139MB. It takes only (1) second to run through it. It takes longer to type out the actual command to run it… The initial crack rate is unimpressive, at 7.5% in our test case, but it runs so fast that it's worth a check.
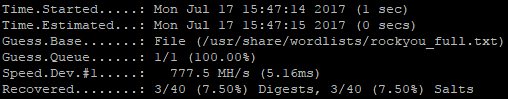
Adding Rules for Better Results
Hashcat has the option to run "rules" against the wordlist, which mangle the words and create more possibilities for cracking. Hashcat comes packaged with several great rules. There are also some community generated rules that are quite useful as well, and most of these get incorporated to the hashcat master branch.
After a couple days' worth of running wordlists/rules combinations and a ton of waiting, we found the most effective wordlists for our test case:
- Append_d: adds numbers to the end of a password, i.e. Password -> Password77
- Append_s: adds special characters to the end of a password, i.e. Password -> Password!
- Leetspeak: changes passwords to leetspeak, i.e. password -> p4$$w0rd
Append_d
Append_d is by far the most effective rule. It added an average of 10% more cracks to each wordlist it was paired with. We'll look at why that is, later in this post, when we analyze some cracked/dumped passwords.
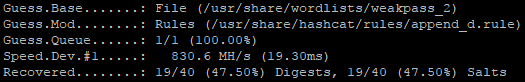
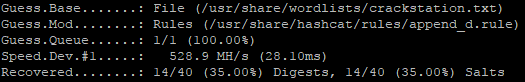
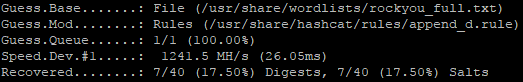
Append_s
Append_s was also pretty effective, adding an average of 6% more cracks to each wordlist it was paired with. This number isn't jaw-dropping, but it could be the difference between pwning or complete frustration.
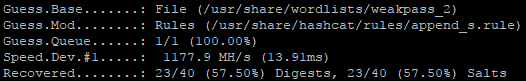
Leetspeak
The leetspeak rule is moderately effective, only adding about 2.5% more cracks to each wordlist it was paired with. However, those passwords have often been admins or service accounts in our recent experiences, so it's worth an extra run through the gauntlet.
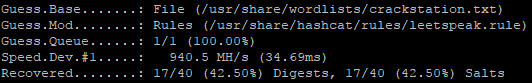
Test case results
Here are the final results from our test case of 40 NTLMv2 hashes:

Analyzing Cracked Passwords
After cracking passwords from our pentests, we like to analyze the password profile to better understand how users generate passwords. To do this, I wrote a quick python script to read the passwords from a given file and spit out some percentages: https://github.com/dank-panda/password-analyzer.py (There is definitely work to be done here, but it'll give you some decent insight for now).
To start, we dump some passwords from a couple recent pentest and run the script against them.
python password-analyzer.py wordlist.txt
We see that 70% of the passwords we analyzed start with an uppercase letter. This isn't a really big surprise. It seems logical to capitalize the first letter, just like we all do for the beginning of a sentence. It's a common practice.
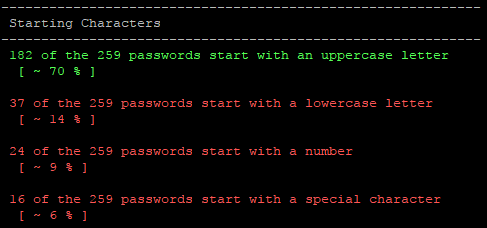
Next, we see is that 61% of the passwords end in a number. This was a surprise to me. I thought that a special character would be the most common, but I was way off the mark on that assumption. It seems reasonable though, given the amount of "Password1" passwords we see. Now we see why the append_d rule was so effective.
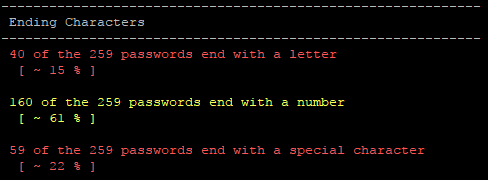
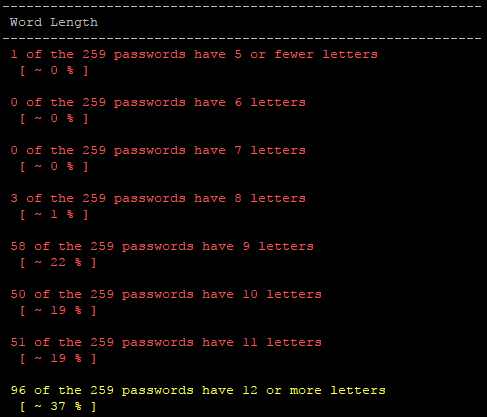
Another big surprise was that most of the passwords were 9+ characters, with 37% having 12 or more characters. This is outside of reasonable brute-force territory. Brute forcing 12 characters with a single 1080 Ti would take roughly a quick 168 BILLION years. Not an option… Kudos unnamed clients.
Another thing we check for, is the use of the company's name in passwords. From the looks of it, people are pretty good about not using their company name as their password. Another win for the users.
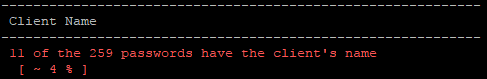
With this quick tidbit of data, we can start to see why the append_d rule adds an average of 10% more cracks. We can focus on identifying better rules and masks for future pentests with more data from dumped passwords, but for now it looks like we're on the right track.
Conclusion
With all the trial and error out of the way, you can now focus creating a "crack plan" to help you more-effectively utilize your cracking time. Our suggested methodology, based on our test case, is as follows:
- Start with the rockyou wordlist
- Run it by itself, then run through the append_d, append_s, and leetspeak rules
- You can run through all 4 attempts in about 30 seconds total.
- The crack rate is unexciting at 22% for all 4 attempts, but for 30 seconds effort, it's WAY worth it.
- Switch to the crackstation wordlist
- Run it by itself, then run through the append_d, append_s, and leetspeak rules (in that order)
- You can run through the all 4 attempts in about 30 minutes. Not too bad for a 15 GB file
- Crackstation, with these rules, had a 42.5% crack rate in our test case. That should be more than enough creds to get started, and the wait isn't unbearable.
- End it with the Weakpass 2.0 wordlist to get those last few potential passwords
- Run it by itself, then run through the append_d, append_s, and leetspeak rules (in that order)
- You can run through the all 4 attempts in about an hour
- Weakpass 2.0 had a 57.5% crack rate in our test case.
With a $1200 build and under 2 hours' worth of cracking effort, we cracked just under 60% of the hashes in our test case. We also know that these passwords are mostly 9+ characters from our password analyzer script. So, they're not necessarily "weak" in entropy regards. Overall, this build isn't out of reach for the hobbyist password cracker, and should provide an effective crack-rate when used with a strong wordlist and rules.
But if you still haven't gotten what you need by this point… you'll have to start trying more advanced techniques, which we'll save for another post.
References
- Weakpass 2.0 wordlist
- https://weakpass.com/download
- Crackstation wordlist
- https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
- Additional wordlists gathered by Daniel Miessler and Jason Haddix
- https://github.com/danielmiessler/SecLists/tree/master/Passwords
- Hashcat Wiki
- https://hashcat.net/wiki/
- Password Analyzer Python Script
- https://github.com/dank-panda/password-analyzer.py